Key Takeaways
- Ethereum’s improve to Proof-of-Stake has sparked issues over the community’s resiliency in opposition to 51% assaults.
- The highest 4 staking entities account for 59.6% of the overall staked ETH.
- Nonetheless, user-activated tender forks (UASFs) be sure that dangerous actors can not take over the community, regardless of how massive their stake.
Share this text
Proof-of-Stake critics have sounded the alarm on Ethereum’s new Proof-of-Stake consensus mechanism, claiming it makes the community vulnerable to hostile community takeovers. Nonetheless, Ethereum’s new system accommodates a failsafe to mitigate this threat and permits customers to burn the funds of any attacker making an attempt to take management of the blockchain.
Ethereum’s Vulnerability to 51% Assaults
Ethereum’s latest swap away from Proof-of-Work has raised questions concerning the community’s skill to fend off assaults.
On September 15, Ethereum efficiently upgraded its consensus mechanism to Proof-of-Stake. Amongst different issues, the occasion, now recognized within the crypto neighborhood because the “Merge,” handed block manufacturing duties from miners to validators. Opposite to miners, which use specialised {hardware}, validators solely have to stake 32 ETH to realize the fitting to course of transactions.
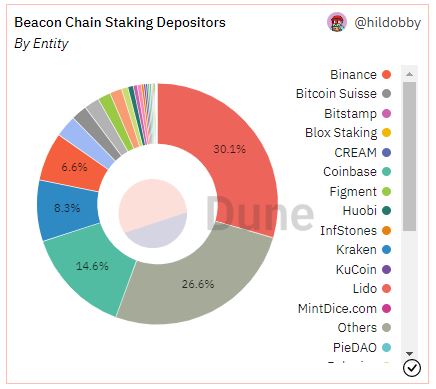
Nonetheless, some crypto neighborhood members have been fast to level out that almost all of Ethereum’s validating energy is now within the palms of just some entities. Knowledge from Dune Analytics indicate that Lido, Coinbase, Kraken, and Binance account for 59.6% of the overall staked ETH market share.
This excessive focus of staking energy has raised issues that Ethereum could also be susceptible to 51% assaults—a time period used within the crypto area to designate a hostile takeover of a blockchain by an entity (or group of entities) in command of nearly all of block processing energy. In different phrases, the concern is that giant staking entities may collude to rewrite elements of Ethereum’s blockchain, change the ordering of recent transactions, or censor particular blocks.
The opportunity of a 51% assault turned notably salient after the U.S. authorities’s ban on Twister Money. On August 8, the U.S. Treasury Division added privateness protocol Twister Money to its sanctions record, arguing cybercriminals used the crypto venture for money-laundering functions. Coinbase, Kraken, Circle, and different centralized entities rapidly complied with the sanctions and blacklisted Ethereum addresses related to Twister Money. So what would stop these firms from utilizing their staking energy to censor transactions on Ethereum’s base layer if the Treasury ordered them to?
As Ethereum creator Vitalik Buterin and different builders have argued, the community nonetheless has an ace up its sleeve: the potential of implementing user-activated tender forks (UASFs).
What Is a UASF?
A UASF is a mechanism by which a blockchain’s nodes activate a tender fork (a community replace) without having to acquire the same old assist from the chain’s block producers (miners in Proof-of-Work, validators in Proof-of-Stake).
What makes the process extraordinary is that tender forks are usually triggered by block producers; UASFs, in impact, wrest management of the blockchain from them and briefly hand it over to nodes (which could be operated by anybody). In different phrases, a blockchain neighborhood has the choice of updating a community’s software program no matter what miners or validators need.
The time period is usually related to Bitcoin, which notably triggered a UASF in 2017 to power the activation of the controversial SegWit improve. However Ethereum’s Proof-of-Stake mechanism was designed to allow minority-led UASFs particularly to struggle in opposition to 51% assaults. Ought to an attacker try to take management of the blockchain, the Ethereum neighborhood may merely set off a UASF and destroy the whole thing of the malicious actor’s staked ETH—decreasing their validating energy to zero.
In actual fact, Buterin has claimed that UASFs make Proof-of-Stake much more proof against 51% assaults than Proof-of-Work. In Proof-of-Work, attackers merely want to amass nearly all of the hashrate to take over the blockchain; doing so is dear, however there is no such thing as a different penalty apart from that. Bitcoin can change its algorithm to render a few of the attacker’s mining energy ineffective, however it could solely achieve this as soon as. Alternatively, Proof-of-Stake mechanisms can slash an attacker’s funds as many occasions as crucial by way of UASFs. In Buterin’s phrases:
“Attacking the chain the primary time will price the attacker many tens of millions of {dollars}, and the neighborhood can be again on their toes inside days. Attacking the chain the second time will nonetheless price the attacker many tens of millions of {dollars}, as they would want to purchase new cash to exchange their previous cash that have been burned. And the third time will… price much more tens of millions of {dollars}. The sport could be very uneven, and never within the attacker’s favor.”
Slashing Is the Nuclear Possibility
When requested whether or not Coinbase would ever (if requested by the Treasury) use its validating energy to censor transactions on Ethereum, Coinbase CEO Brian Armstrong said that he would somewhat “deal with the larger image” and shut down the change’s staking service. Whereas there’s little motive to doubt the sincerity of his reply, the potential of a UASF seemingly performed a task within the equation. Coinbase at the moment has over 2,023,968 ETH (roughly $2.7 billion at right this moment’s costs) staked on mainnet. The change’s whole stack might be slashed if it tried censoring Ethereum transactions.
It’s vital to notice that slashing isn’t Ethereum’s solely choice in case of a malicious takeover. The Ethereum Basis has indicated that Proof-of-Stake additionally allows trustworthy validators (that means validators not making an attempt to assault the community) to “preserve constructing on a minority chain and ignore the attacker’s fork whereas encouraging apps, exchanges, and swimming pools to do the identical.” The attacker would preserve their ETH stake, however discover themselves locked out of the related community going ahead.
Lastly, it’s value mentioning that Ethereum’s staking market isn’t fairly as centralized as it could initially appear. Lido, which at the moment processes 30.1% of the overall staked ETH market, is a decentralized protocol that makes use of over 29 totally different staking service suppliers. These particular person validators are those in command of the staked ETH—not Lido itself. Thus, collusion between main staking entities could be way more troublesome to arrange than it will initially seem.
Disclaimer: On the time of writing, the writer of this piece owned BTC, ETH, and several other different cryptocurrencies.

