Key Takeaways
- Harpie is the primary on-chain firewall product that protects customers towards widespread assault vectors in crypto.
- It really works by monitoring customers’ wallets and intervening in case of an assault by frontrunning malicious transactions and transferring their funds to a safe non-custodial vault.
- Whereas it isn’t good, it is one of the promising choices for shielding Web3 customers in existence at present.
Share this text
Harpie’s on-chain firewall lets crypto customers join their Web3 wallets and create a protected transacting atmosphere and shield themselves towards crypto’s most typical assault vectors.
Crypto’s Safety Drawback
As crypto and decentralized finance have risen in reputation during the last couple of years, so have cryptocurrency-related assaults, together with focused person thefts and protocol exploits. Based on Chainalysis‘ mid-year crypto crime report, over $1.9 billion had been stolen in hacks of customers and companies from January by means of July 2022, up from just below $1.2 billion over the primary seven months of 2021. And whereas a lot of the exploits have been protocol-related, many customers have had their wallets drained thanks partially to the dangers related to utilizing Web3 at present.
For customers who repeatedly work together with DeFi protocols and NFT marketplaces, transacting in Web3 can nearly really feel like taking part in Minesweeper in actual life. Each transaction approval and on-chain interplay with a third-party utility can doubtlessly result in pockets compromise and lack of funds. Sadly, there hasn’t been a easy or environment friendly answer to this drawback up to now. The most well-liked Web3 wallets, like MetaMask or Belief Pockets, do an abysmal job of conveying the character of every on-chain interplay to their customers. As a substitute of constructing every transaction clear, the default descriptions of most in-wallet transaction confirmations learn like gibberish to most unsophisticated customers, leaving them successfully blind to even essentially the most fundamental safety threats.
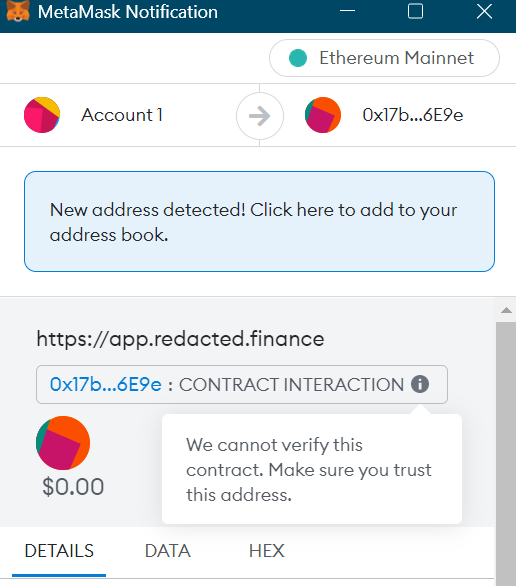
Past the same old protocol hacks, maybe essentially the most harmful kind of assaults affecting crypto customers are so-called “approve spend” exploits that trick customers into approving malicious transitions that permit the hackers to empty the customers’ wallets. One other widespread approach Web3 customers lose their cash is by having their personal keys compromised, which generally includes customers putting in malicious software program like keyloggers, storing their seed phrases in plain textual content on insecure gadgets, or falling for phishing scams.
Defending towards all of those assault vectors has at all times been attainable, but it surely requires vital technical information, sophistication, and sacrifices in person expertise. Harpie is hoping to resolve this drawback.
What’s Harpie?
Harpie is the primary on-chain firewall answer that lets Ethereum customers create a protected transacting atmosphere by whitelisting a set of addresses and Web3 purposes they deem protected. The service displays linked wallets for pending suspicious or unpermitted transactions to cease them after they floor. When it detects a suspicious transaction, it instantly strikes the person’s funds out of their pockets and right into a protected, non-custodial vault, defending the funds from potential theft.
Harpie does this by frontrunning malicious transactions by paying the next gasoline price. For instance, suppose a hacker has by some means gotten maintain of a person’s personal keys or fooled them into approving a malicious spending transaction and tried to switch funds from the sufferer’s pockets into his tackle. In that case, Harpie would detect the outgoing transaction from the sufferer’s pockets to an unapproved tackle, and routinely broadcast one other transaction with the next gasoline price to maneuver the goal’s funds right into a protected vault earlier than the outgoing transaction is confirmed.
Ethereum validators prioritize transactions with the very best gasoline charges, which implies they’ll choose up and make sure Harpie’s benevolent transactions earlier than any attackers, thus saving customers from theft.
After Harpie has intervened and moved the belongings to a protected place, the person can withdraw them to a brand new uncompromised pockets for a flat price of 0.01 ETH, whatever the quantity that was saved within the process.
How one can Use Harpie
Customers should join their present Web3 pockets to Harpie to make use of the service. They’ll do that by clicking the “Enter App” button within the high proper nook of Harpie’s homepage after which clicking “Join” inside the appliance. Customers additionally want to verify the connection inside their wallets individually to present Harpie permission to observe their wallets and transfer funds from them in case of an incident.
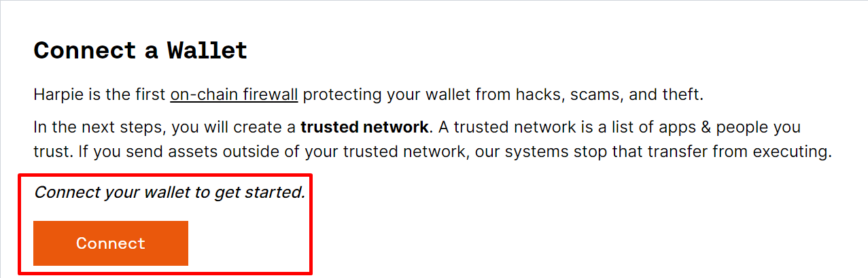
After connecting, customers are requested to arrange their “Trusted Community” of purposes and addresses. These are purposes and addresses the customers deem protected and want to exclude from the firewall, which means Harpie gained’t routinely block any transactions with them.
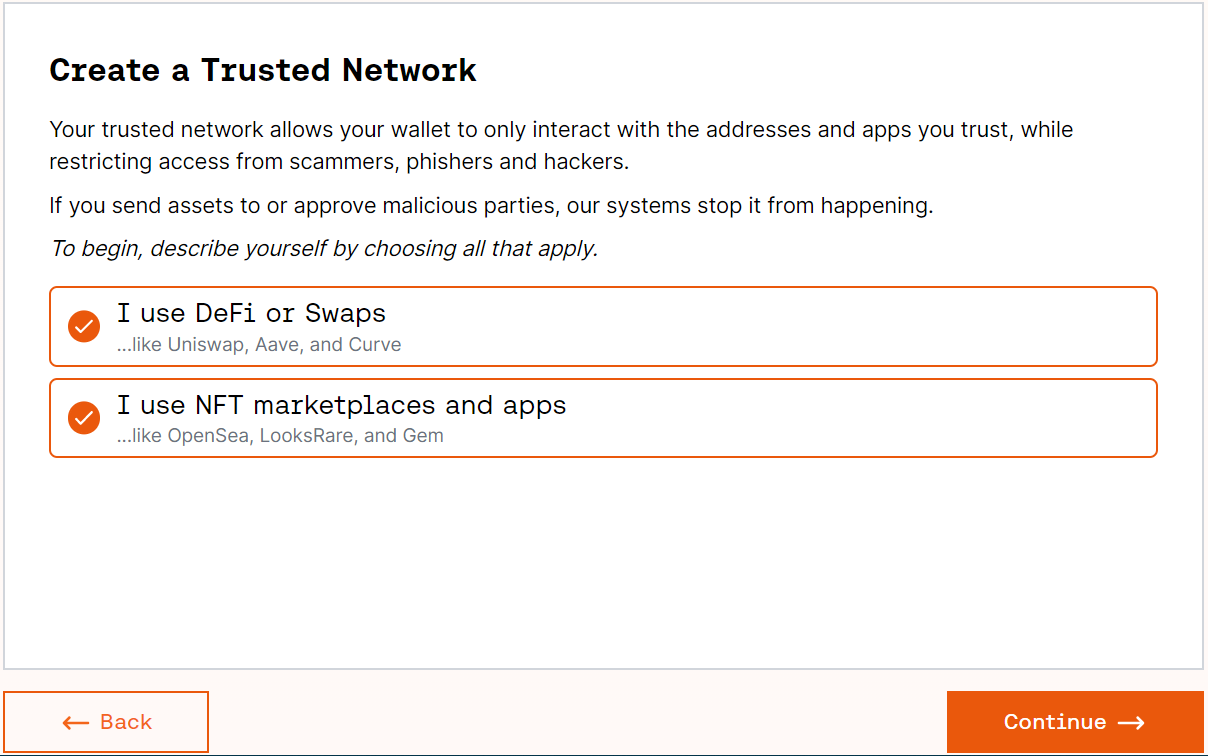
To do that, customers can select in the event that they use DeFi purposes, NFT marketplaces, or each and choose their trusted community of purposes from a preselected record of established protocols. All the protocols that Harpie recommends by default have undergone in depth auditing, stood the take a look at of time, and are typically thought-about safe, which means customers ought to really feel protected about whitelisting all of them. After choosing the trusted set of purposes, customers should press “Proceed” within the backside proper nook and signal the transaction inside their pockets.
Upon signing, Harpie will begin integrating its firewall system with the person’s pockets, and after it’s completed, customers will probably be directed to their dashboard. There, they’ll navigate to the “My Trusted Community” tab and add all of the addresses they’re repeatedly interacting with underneath the “Buddies” part. These might embody their very own private wallets, their mates’ wallets, and the deposit addresses of the centralized exchanges they use.
Customers should additionally allow Harpie to entry their pockets’s funds to have the ability to transfer them to a safe vault in case of an assault. They’ll do that by clicking “Defend” for every asset of their dashboard’s “Protected Belongings” part. If they’ll’t see all of the belongings they’re holding of their pockets, they’ll import them manually from the identical dashboard part.
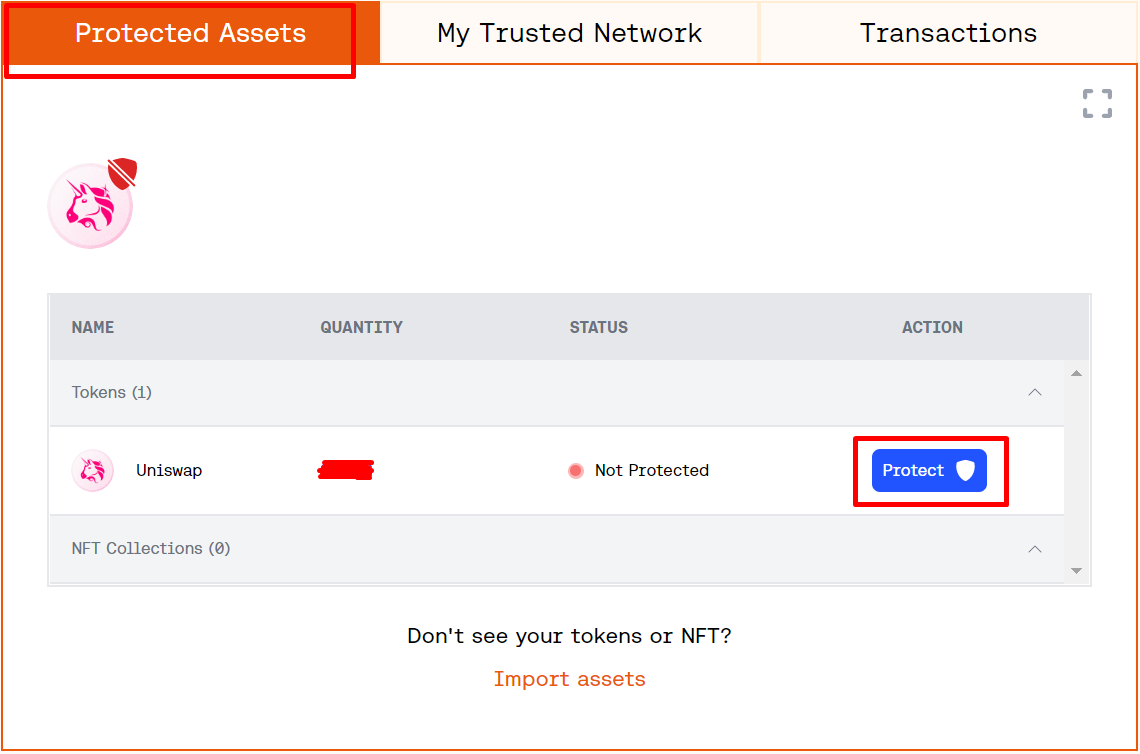
Clicking “Defend” for every asset is essentially the most essential process for each person utilizing Harpie. It’s because whitelisting a trusted community of purposes and addresses solely tells Harpie what visitors to observe, whereas allowing it to entry the pockets’s funds is what truly permits it to intervene and transfer the belongings to a protected place in case of an assault.
Lastly, customers have to arrange a withdrawal tackle that may have the flexibility to retrieve the funds moved to the protected vault in case Harpie has intervened throughout a safety breach. They’ll do that by clicking on the “Setup” button within the “Setup withdrawal tackle” part, coming into the tackle they wish to use for retrieving funds, clicking “Register,” after which approving the motion with their pockets.
It’s essential to make clear that Harpie can solely shield customers from dropping belongings they have already got of their wallets. If customers deposit or stake their belongings on a third-party crypto protocol and the appliance will get hacked, Harpie gained’t be capable to do something to guard the customers’ funds.
Ultimate Ideas
Whereas no single system or protocol can clear up crypto’s safety drawback, Harpie’s on-chain firewall method provides a vital layer of safety to the each day operations of the extra lively Web3 customers. Past protocol hacks and sure edge instances, Harpie can successfully shield customers towards nearly widespread crypto exploits with out severely impeding their person expertise.
With that mentioned, interacting with Web3 with Harpie’s firewall answer nonetheless introduces some inevitable hindrances from a person expertise standpoint. For instance, customers might overlook to whitelist their pal’s tackle or their very own account on a centralized trade and have their belongings routinely moved to Harpie’s non-custodial vault after they try to make an intentional switch. Past that, Harpie additionally doesn’t present customers with a easy strategy to revoke the firewall’s entry. As soon as enabled, customers want to make use of a third-party utility like revoke.cash to revoke the entry they’ve given to Harpie in the event that they want to opt-out of it.
Every little thing thought-about, Harpie supplies a much-needed on-chain safety layer that customers at the moment can’t discover wherever else. Whereas Harpie isn’t good at present, its answer is a transparent step in the best course towards making Web3 safer for normal customers.
Disclosure: On the time of writing, the creator of this text owned ETH and a number of other different cryptocurrencies.

